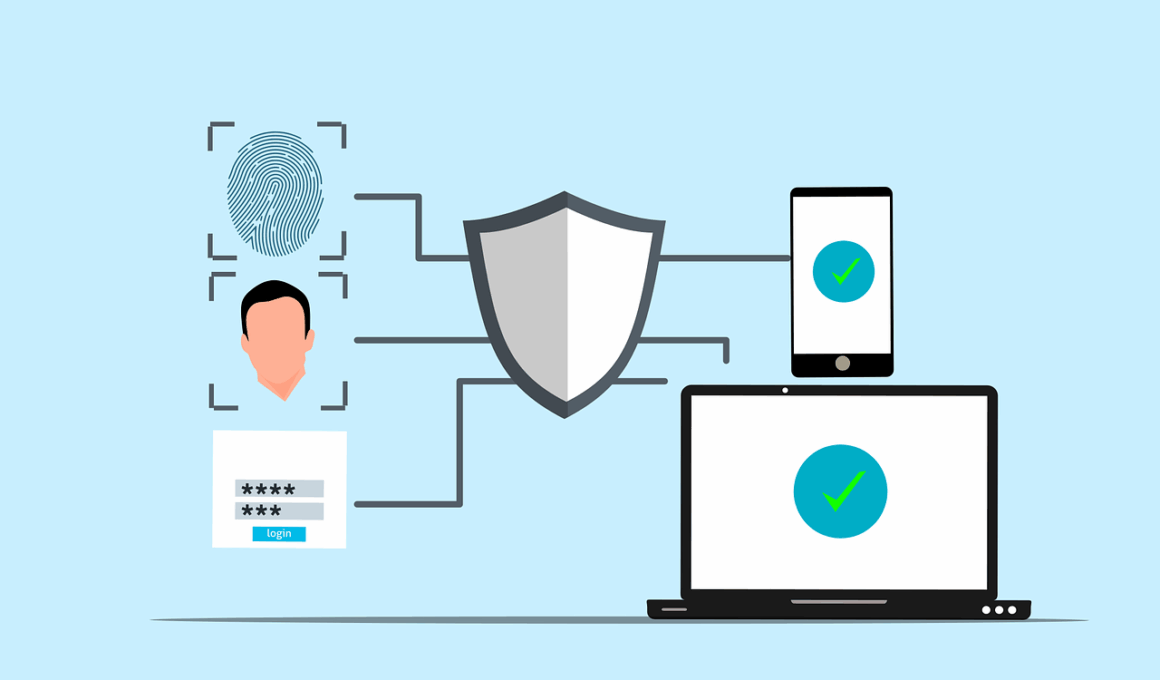
Emerging Trends in Cloud Security Affecting Business Risk Management
In today’s digital landscape, organizations are increasingly migrating to cloud environments, thereby reshaping the way businesses manage security protocols. Cloud security has become a critical focus, as companies aim to safeguard sensitive data while maintaining compliance with regulations. Emerging technologies, such as artificial intelligence and machine learning, are enhancing cloud security measures designed to detect and respond to threats in real-time. Companies must prioritize implementing advanced encryption techniques, robust access controls, and continuous monitoring to protect their cloud assets. Additionally, adopting a zero-trust approach can bolster security postures, ensuring that every access request is validated before granting permissions. It is imperative that businesses invest in staff training to understand the complexities of cloud security, as human error remains a significant vulnerability. Cloud service providers also play a pivotal role in securing their platforms, making it essential to choose reliable partners for cloud services. As the threat landscape continues to evolve, staying abreast of security trends is vital for businesses to proactively mitigate risks associated with cloud computing and protect their critical information assets.
Part of the emerging trends in cloud security involves the rise of cloud-native security tools, which are designed specifically to protect data stored in the cloud. Organizations are increasingly leveraging these tools to enhance detection, response, and remediation capabilities across their cloud environments. These solutions can provide greater visibility and situational awareness, allowing businesses to identify suspicious activities and respond swiftly to potential threats. Emphasizing automation in cloud security is now more critical than ever, as it reduces the burden on security teams while enhancing overall efficiency. Furthermore, organizations are concentrating on implementing Identity and Access Management (IAM) systems to ensure that only authorized personnel can access sensitive data. IAM plays a crucial role in minimizing risks associated with unauthorized access. By integrating IAM solutions, businesses can gain better control over user identities, and permissions, thus reducing the potential for insider threats. Moreover, with the increased adoption of multi-cloud environments, organizations must ensure security measures are consistent across various cloud platforms. This consistency is essential for maintaining comprehensive security and compliance, safeguarding company information, and protecting against evolving cyber threats.
The Role of Compliance in Cloud Security
Compliance continues to be a major consideration for businesses utilizing cloud services, particularly with the constant evolution of regulations and standards related to data protection. Regulations like GDPR, HIPAA, and CCPA impose strict obligations on organizations regarding data handling, storage, and security. Consequently, organizations must ensure that their cloud security policies align with relevant legal requirements to avoid severe consequences, including penalties and reputational damage. Implementing comprehensive governance frameworks can aid organizations in navigating the complex compliance landscape. These frameworks should clearly define roles, responsibilities, and procedures related to data protection in the cloud environment. Additionally, regular audits and assessments should be conducted to identify any gaps in compliance. Businesses must also maintain detailed records of data processing activities and user consent, as these will be essential in demonstrating compliance during regulatory inspections or audits. Moreover, ensuring that cloud service providers are also compliant with relevant regulations is crucial. Partnering with vendors that prioritize compliance can help minimize risk and ensure that data privacy and protection standards are upheld across the entire organization.
Another trend reshaping cloud security is the growing importance of incident response and disaster recovery plans. In the event of a security breach or data loss, having a robust incident response plan in place is essential for ensuring that organizations can recover quickly and minimize operational disruption. Businesses should develop and regularly update their incident response protocols to reflect new threats. They should also conduct frequent simulations and drills to ensure readiness among their teams. Disaster recovery plans also play a crucial role in safeguarding business continuity, enabling organizations to restore data and applications swiftly. This involves creating backups in separate environments and ensuring that recovery procedures are well-documented and tested. Moreover, organizations must consider the implications of ransomware attacks, where data is encrypted, and a ransom is demanded. Investing in preventive measures, such as network segmentation and regular software updates, can help reduce the likelihood or impact of such incidents. Fostering a culture of security awareness within the organization is also vital, as employees are often the first line of defense against potential security threats.
The Impact of Remote Work on Cloud Security
The transition to remote work has significantly influenced cloud security considerations, as employees access corporate resources from various locations and devices. This shift necessitates robust security measures to ensure that sensitive data remains protected while employees work remotely. Organizations are increasingly implementing Virtual Private Networks (VPNs) and using multi-factor authentication to create secure connections for remote workers. Additionally, endpoint security solutions are becoming essential to monitor and protect devices accessing the corporate network. These solutions help safeguard against malware, phishing attacks, and data breaches, ensuring the integrity of company information. Implementing security awareness training programs is also critical, as educating employees on best security practices can significantly reduce risks. Moreover, businesses should regularly review and update their remote work policies to reflect emerging threats and vulnerabilities. By establishing clear guidelines for remote access and data handling, organizations can reduce the risk of insider threats and unauthorized access. The trend toward remote work is expected to continue, making it essential for businesses to prioritize cloud security to enable secure remote access without compromising data protection.
As organizations continue to shift towards cloud computing, the importance of third-party risk management cannot be overlooked. Engaging with cloud service providers introduces inherent risks, particularly regarding how they handle security and compliance. Businesses must thoroughly vet their providers to assess their security postures and compliance with relevant regulations. Implementing third-party risk assessments will provide valuable insights into the security practices of vendors. Furthermore, establishing clear contractual obligations around security can ensure that vendors adhere to stringent protocols. Regular monitoring and communication with providers are equally important; organizations should maintain ongoing dialogue to stay informed about potential vulnerabilities. This collaboration fosters a partnership that prioritizes security and compliance, ultimately benefiting both parties. Additionally, organizations must consider the risk posed by shadow IT, where employees use unauthorized applications or services that can compromise security. Developing policies that discourage shadow IT and promoting approved tools is crucial in limiting potential risks. By managing third-party risks effectively, companies can bolster their overall cloud security strategy, ensuring that their data remains safeguarded from undesirable threats and vulnerabilities.
Conclusion: Adapting to the Future of Cloud Security
In conclusion, adapting to emerging trends in cloud security is imperative for effective business risk management. Cloud security will remain a dynamic field influenced by advancements in technology and evolving threat landscapes. Businesses must stay attuned to these changes to modify their security strategies accordingly. This involves integrating sophisticated machine learning algorithms and automation to bolster their defenses against cyber threats. Furthermore, organizations should prioritize cloud security as a core aspect of their overall IT strategy rather than viewing it as a mere compliance requirement. Investing in skilled professionals who specialize in cloud security will enhance an organization’s ability to respond effectively to incidents. Businesses must embrace collaborative efforts with trusted partners to create a comprehensive security ecosystem. In such an ecosystem, all stakeholders share knowledge, resources, and best practices to fortify cloud security. Continual reassessment of security measures is essential; by staying proactive, organizations can mitigate risks and ensure that their cloud environments remain safe and resilient against future threats, enabling sustainable business practices in a digital world.
Organizations that want to enhance their cloud security posture must also consider adopting a comprehensive cyber insurance policy. Such policies can help mitigate financial losses arising from data breaches and cyber incidents. Cyber insurance can provide coverage for costs associated with investigations, notifications, legal fees, and regulatory fines. As businesses increasingly rely on cloud services, understanding the terms and conditions of these insurance policies is vital. Companies should work closely with insurers to ensure that the coverage aligns with their cloud security practices and risk profiles. Moreover, reviewing and updating coverage regularly can help organizations stay aligned with their evolving risk landscape. Investing in cyber insurance should be complemented by proactive cybersecurity measures, as it does not eliminate risks but rather helps organizations manage them more effectively. By creating an integrated approach combining strong security measures with cyber insurance, organizations can ensure they are prepared to face unforeseen incidents. This strategy not only protects the organization but also ensures clients and stakeholders feel secure knowing that due diligence is exercised to safeguard sensitive information while embracing cloud technologies.